How Your Cellphone Can Be Used Against You
Have you ever heard the term De-Googled? Basically, it is when an Android™ phone is customized to remove everything proprietary (i.e., Google Play services and vendor-specific closed-source additions.)
Google tracking is an invasive form of data collection. For an eyeopener of what it records, you can find a complete history of your Google account.
Former NSA consultant Edward Snowden alerted the public to the fact that three-letter government agencies were conducting mass surveillance on the general population by listening to their phone calls. Consumers need solutions to increase their mobile phone privacy. Especially when big tech companies and social media platforms are used to create unrest and division. With this level of interference, your cell phone can be a personal security risk.
Travellers, likewise, are alarmed to know their mobile devices can be seized when clearing customs or at border crossings. Airport agents can request owners unlock their phones without a warrant. If you comply, they’ll run your data through an algorithm on their system. They may not find anything to detain you, but it is an affront to your privacy. If you don’t comply, you could be arrested. People are rightly worried about these infringements on their rights.
There are several application processing interfaces on mobile phones that can be used to collect data. Mobile apps and social media accounts are notorious for their user data policies. Behavioural data is shared by social media companies and sold to third parties.
Electronic Frontiers Foundation notes in its Surveillance Self-Defense guide, “The deepest privacy threat from mobile phones—yet one that is often completely invisible—is the way that they announce your whereabouts all day (and all night) long through the signals they broadcast.
There are at least four ways that an individual phone's location can be tracked by others.
- Mobile Signal Tracking from Towers
- Mobile Signal Tracking from Cell Site Simulators
- Wi-Fi and Bluetooth Tracking
- Location Information Leaks from Apps and Web Browsing
Software Developers Kits used in mobile phone apps can be set up to track you. A mobile advertising identifier, or MAID, is a unique ID on your phone. It can’t be removed unless you use a secure phone.
Methods Used By Malicious Actors
Spyware can be inadvertently downloaded on your phone, such as the weaponized zero-day vulnerability exploited in Google Chrome that recently targeted journalists in Lebanon. Mobile devices can assist subversive players in locating and identifying users in many ways, from cell tower triangulation to surveillance with tracking devices like Stingrays.
Privacy experts warn about posting too much data online. Social engineering tactics that gather personally identified information on individuals from social media accounts can be used for harassment online or by messaging, phone, email, and even in person. This kind of attack is called doxing. It is often in retaliation for an action or even a political opinion that the threat actor is using against the target or the individual’s family members.
As far back as 2015, the FBI reported that elections officials have been doxed simply for being involved in the democratic process. “Doxed victims report receiving harassing phone calls, faxes, and emails, having compromised credit cards used to harass them, having strangers sit outside their house, and having phone calls made on their behalf. It can result in innocuous activities, such as having a pizza ordered, but it can also result in life-threatening activities, such as a call to 9-1-1 claiming an intruder, who looks like the victim, is committing a crime at the victim’s current location.”
In America, since Roe v. Wade was overturned, women and doctors alike are at risk of having their cell phones scrutinized over abortion care. Lawyer Albert Cahn is the founder of the Surveillance Technology Oversight Project. He notes, “In 2022, electronic surveillance and device searches are an everyday part of American policing. Officers submit warrants to Google by the tens of thousands. … Nearly every app on our phone is collecting information that can potentially be used.”
Cahn added, “We continue to be very fearful that activists and law enforcement can monitor clinic entrances using automated license plate readers, using facial recognition, using other forms of biometric surveillance. These tools have truly gotten out of control.”
Your data is valuable to hackers online. But a data breach can also result in legal repercussions for you personally. Professionals who text colleagues with private corporate or client information may face regulatory consequences. In many countries, leaked data could make you personally responsible.
Take Canadian physicians, for example. “Texting patients’ identifiable personal health information may lead to a privacy breach. Privacy legislation requires custodians of personal information, including health information, to safeguard that information from theft, loss, and unauthorized use or disclosure.”
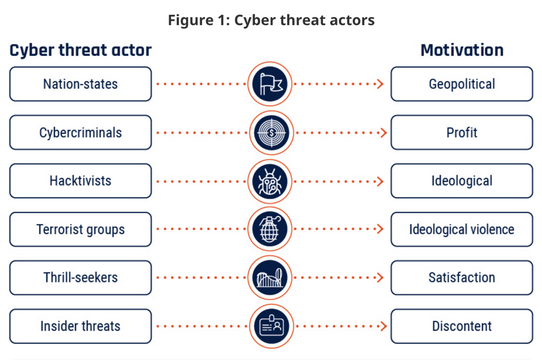
The Canadian Centre for Cyber Security lists the types of cyber threat actors and their motivations stating, “Some threat actors conduct threat activity against specific individuals or organizations, while others opportunistically target vulnerable systems.” Most mobile devices are extremely vulnerable due to the use of apps, public Wi-Fi, Bluetooth, GPS, and a general lack of security.
How To Safeguard Your Communications
The following are signs that your device has been hacked.
- Unusual data usage spikes
- Excessive battery drainage
- Takes forever to launch apps
- Restarts for no reason
- Weird popups
- Background noise
- Apps that you don't remember installing
- Strange phone calls
- Unusual activity on the accounts connected to your phone
If you believe your cellphone has been hacked, authorities say you should get professional assistance. “Be sure to consult with an IT security professional immediately if you think that your device or account has been hacked. Users of corporate devices should contact their IT department; users of personal devices should contact a reputable IT service provider.”
If you’re looking for an encrypted mobile solution trusted worldwide for personal and business communications, discover the difference of a truly secure phone versus a privacy tool like WhatsApp.
ChatMail™. Engineered for Security. Designed for Privacy.

 ChatMail | December 15, 2022
ChatMail | December 15, 2022